Tel: 01474 876800 • 24 Hr: 01474 876809 • Client Portal
- Who We Are
- What We Do
- Build
- Carpentry
- Building Works
- Commercial Flooring
- Commercial Glazing
- Commercial Locksmith
- Commercial Painting & Decorating
- Commercial Plastering
- Commercial Plumbing
- Commercial Refurbishment
- Commercial Roofing
- Design & Construction
- Electrical Installation
- Hard & Soft Landscaping
- Mechanical & Electrical
- Office Builders
- Office Fit Outs
- Office Heating
- Office Partitioning
- Office Relocation
- Site Management
- Maintain
- 24 Hour Helpdesk
- Access Control
- Air Conditioner Repair
- Air Conditioning Servicing
- Commercial Boiler Servicing
- Commercial Electricians
- Commercial Ground Maintenance
- Commercial Pest Control
- Commercial Property Maintenance
- Drain Unblocking
- Emergency Callouts
- Emergency Light Testing
- Facilities Management
- Fire Alarm Testing
- Fire Extinguisher Testing
- Fire Sprinkler Testing
- Fixed Wire Testing
- Handyman Service
- Lift Servicing
- Office Health & Safety
- PAT Testing
- Planned Preventative Maintenance
- Reactive Maintenance
- Roof Maintenance
- TMV Maintenance
- Water Hygiene
- Clean
- Build
- How We Do It
- Why Use Us
- Contact

What is Access Control?
Controlling who accesses data or who is allowed to enter into a particular part of a premises is of utmost importance to an organisation’s integrity, and to safeguard resources.
Data security is of imperative importance, especially nowadays where privacy and confidentiality are being given priority.
Access control is an integral part of security measures.
Table of Contents
What is Access Control?
Access control refers to the policies and measures that are implemented to ensure that organisational resources are only accessed by those who have a right or authority to access them.
Hence authorisation and authentication are part and parcel of access control.
In simple words, access control is a way of guaranteeing that a user is really who they say they are.
And depending on this identity verification, they will then be granted access to the data or other resources.
How Access Control Works
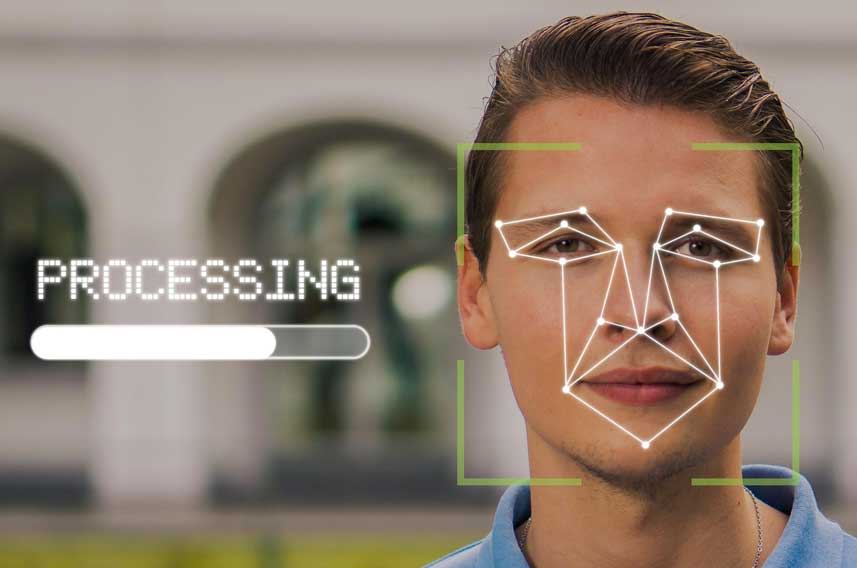
Access control includes the identification of users, following the verification of their login credentials.
These could vary considerably.
Traditionally, it was merely a physical identification method, such as showing an ID tag or swiping an access card.
Now, it’s often not just something that one owns, but also something unique to them, with some common examples being a username and password, or a PIN number.
Now there’s even more advanced methods like biometric scanning, using facial recognition, fingerprints or iris scanning.
In such cases of biometric identifiers, it’s essentially something that’s integrally unique to the person, so it’s even more secure.
Each identification method has its respective pros and cons.
As a result, two-factor or multi-factor authentication has gained popularity in recent times to provide an additional layer of security.
As soon as a user is authenticated, access control will ensure that they are given the appropriate level of access accordingly.
Types of Access Control

It’s important for an organisation to decide which of the following models is most suitable.
This will depend on data sensitivity and the operational requirements associated with data access.
There are four main types of access control, namely:
1. Discretionary access control (DAC)
This refers to when the administrator sets the policies of who is allowed to access the system or data, according to their discretion and any rules that are set by this person.
2. Mandatory access control (MAC)
In this case, people are granted access on the basis of information clearance.
There will be a central authority which will regulate the access rights according to various security levels.
This is a commonly used method in military settings as well as in government institutions.
3. Role-based access control (RBAC)
Access is granted according to the business function one has.
Hence, users will access data if it’s deemed necessary to their particular role in the organisation.
The role of the individual is the key here, and as a result security principles will be implemented according to the level of privilege one is deemed to have.
4. Attribute-based access control (ABAC)
In this case, access will be based on specific attributes and environmental conditions.
These could include the time of day, and the location.
Hence this is a dynamic method.
Why Access Control is Important
Access control is of utmost importance as it ultimately regulates who can and cannot have access to the system and any sensitive data.
It is the way in which confidential data is kept private, and only accessed by people who have a right to access it.
The safety of intellectual property is of critical importance, and if it weren’t for proper access control measures, serious repercussions could ensue.
In fact, when data leakage cases occur, the consequences are often very serious.
Access control is particularly crucial for those organisations where multi-cloud and hybrid cloud environments exist.
When the data, apps and other resources are in the cloud, it’s even more critical for proper access control mechanisms to be in place.
Nowadays, access control is of critical importance for most businesses since many workers are now working remotely.
When employees connect to the internet and attempt to log in and access data and resources, it’s critical to ensure that they’re indeed authorised to do so.
Reasons for Strong Access Control

Strong access control is critical in ensuring that data and resources are only accessed by authorised personnel.
Nowadays, access control is even more critical because we are living in an ever-changing world.
Many people work in hybrid environments, and consequently data moves from servers in the organisation’s premises, to offices, as well as homes, cars, coffee shops, or wherever the particular employee is working from.
Besides the locations, there is also the issue of the devices used.
One employee may use a laptop, or a PC, or a smartphone or tablet.
Hence this huge range of connected devices presents a challenge to those who are setting up access control policies.
Another key reason why access control is so important is to prevent cases of access mining.
Sensitive information such as usernames, passwords and domain information are mined.
The collecting and selling of such access descriptors is unfortunately quite common among cybercriminals.
Access control technologies thus need to be consistently supported and maintained.
Any threats need to be identified in real time, and access control rules should be automated accordingly in an instantaneous manner.
Access Control Systems vs Physical Keys
When it comes to a physical access control system, users will typically have an access card or some form of physical key which grants them access to certain areas within the premises.
Physical or mechanical keys are the simplest or most traditional form of access control.
As organisations grow bigger and more complex, and as more employees are involved, physical keys are no longer ideal.
Besides the possibility of loss or theft, physical keys can easily be misused.
Audit trails are not possible either.
Hence, the switch to electronic access control systems has become much more common in many organisations.
Access control systems improve control mechanisms, and enhance privacy, besides limiting the drawbacks of using physical keys.
Benefits of Access Control Systems
There’s no denying that access control systems are of utmost importance.
It’s impossible to imagine any organisation operating safely and efficiently without a proper access control system in place.
Access control systems provide various benefits, including:
- Keeping resources secure.
- Preventing theft and restricting access.
- Increasing control.
- Ensuring that confidential information or areas are only accessed by authorised personnel.
- Incorporates various mechanisms to continuously verify access.
- Varying levels of security are possible.
- Reduces instances of data leakages.
- Thanks to integration with all systems, optimum security and efficiency can be achieved.
Conclusion
To effectively protect your data and resources, it’s crucial to have an access control policy that works well.
It is recommended that due consideration and advice from an expert in the field is taken, to choose a system that will ensure effective control and efficiency.
However, besides setting up such a system, it’s also critical that it’s constantly monitored too.
This includes ensuring that there’s proper compliance, and that any possible security holes are identified as soon as possible.


Request a Callback
Recent Posts
- How to Clean an Oven 01th Apr 2023
- How to Clean & Descale a Shower Head 01th Mar 2023
- How to Clean a Fabric Sofa 01th Feb 2023
- How to Get Rid of Mould 01th Jan 2023
- How to Clean a Mattress Properly 01th Dec 2022
- How to Clean a Washing Machine 01th Nov 2022
- How to Clean a Microwave 01th Oct 2022
- How to Get Blood Out of a Carpet 01th Sep 2022
- What is Access Control? 01th Aug 2022
- What is Hot Water Extraction Carpet Cleaning? 01th Jul 2022

